Cowpatty 2 0 Windows 10
Cracking a wireless network is defeating the security of a wireless local-area network. When all 8 bits of the removed byte were zero, the CRC of the shortened. LEAP uses a variation of Microsoft Challenge Handshake Protocol version 2. Aircrack-ng runs on Windows and Linux, and can crack WEP and WPA-PSK. Download coWPAtty para Windows 4.0. A Free (GPL) Browsers program for Windows.
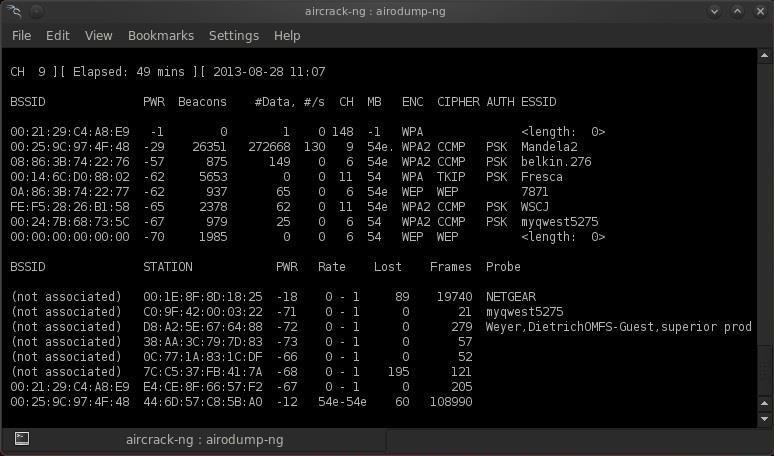
A single network data capture file (pcap format) can contain more than one handshake. This can happen, for example, with the continued capturing, as a result it can got several handshakes from one or more access points. Handshakes from files captured in ‘noisy’ conditions need additional verification and cleaning. Several handshakes in one file can be obtained artificially, simply by combining them into one file. For example, the program (automatically captures handshakes from all access points within reach, for this purpose conducts deauthentication attack) creates a single.cap file for all captured handshake packets. Therefore, this is not a rare situation, and to perform an attack on the wireless networks, whose handshakes are in the same file, you may need to extract each handshake. How to separate handshakes on different files It is important to understand the difference between a file in which several handshakes are simply merged and a capture file in a noisy environment.
An example of analyzing a file of the first type (using ): aircrack-ng FILE_NAME.cap File example of the second type: It can be seen that there is a lot of garbage in the second file, and in the whole file there are only two handshakes suitable for hacking. Among the garbage, there are many separate EAPOL frames (components of a handshake) that are unsuitable for password cracking. To view the contents of a file, you can use Wireshark. After opening the file, apply the filter: eapol Manual separation handshake files using Wireshark If you work with a file from merged handshakes, then there should not be any problems with it. Open the file in Wireshark.
You can use a filter wlan.fc.type_subtype == 0x08 wlan.fc.type_subtype == 0x05 eapol But it may not be necessary, because there are already only the necessary packages. To filter packets for a specific access point, specify the BSSID with the following filter: wlan.addr==BSSID For example: wlan.addr==28:28:5D:6C:16:24 Or so: wlan.fc.type_subtype == 0x08 wlan.fc.type_subtype == 0x05 eapol && wlan.addr==28:28:5D:6C:16:24 Now use CTRL+m to select the required packages: And from the File menu, choose Export Specified Packets: Enter the file name and put the switch on the Marked packets only: Checking our file. All perfectly. You can make another check with by running a command like this: cowpatty -r FILE -s ESSID -c For example, in my case: cowpatty -r ZyXEL_59.pcap -s ZyXEL_59 –c The phrase ‘Collected all necessary data to mount the crack against WPA2/PSK passphrase’ means that all the necessary data is collected to crack the password. To isolate the handshake from a capture file made in noisy conditions, it is necessary to exert some effort. The fourth set (orange): there is no second message. The fifth set (green) is suitable, because there is a second and the first message.
The time between messages seems acceptable. Select and save the necessary frames (I also include a Beacon frame): Our file is being tested: Extracting a handshake with tshark tshark is Wireshark, but without a graphical interface.
This program can also be used to separate a large capture file into separate handshakes.
Designer fonts free download 2015. Just another IT Security Researcher by Many tools exist in order to speed up the cracking process and in this lesson we are going to look at Cowpatty or “coWPAtty” created by a security researcher called along with another tool called genpmk also created by Joshua. First the Pre-Shared Key (PSK) or Pairwise Master Key (PMK) This can be a very time consuming task calculating the Pre-Shared Key using the CPU, you can also use a GPU but for now we are working off the CPU on the Raspberry Pi. The Pre-Shared Key is derived from the WPA/WPA2 passhrase in this lesson “password12345” along with the SSID which is “test”. The combination of the passhprase and the SSID are passed through the “Password Based Key Derivation Function” or PBKDF which then outputs a 256 bit Pre-Shared key (PSK). After this the cracking involves using the 256 bit PSK with the four-way handshake and verifying it against the Message Integrity Code also known as the MIC or referred to as the “Michael” which is there to prevent against forgery attacks. These parameters vary in the handshake every time therefore this step cannot be precomputed.